Learn to recognise and identify scams, so you don’t get cheated The Macau scam is fairly well known today -...


Learn to recognise and identify scams, so you don’t get cheated The Macau scam is fairly well known today -...

Business Email Compromise Scams Are On The Rise There has been a surge in business email compromise (BEC) or email...
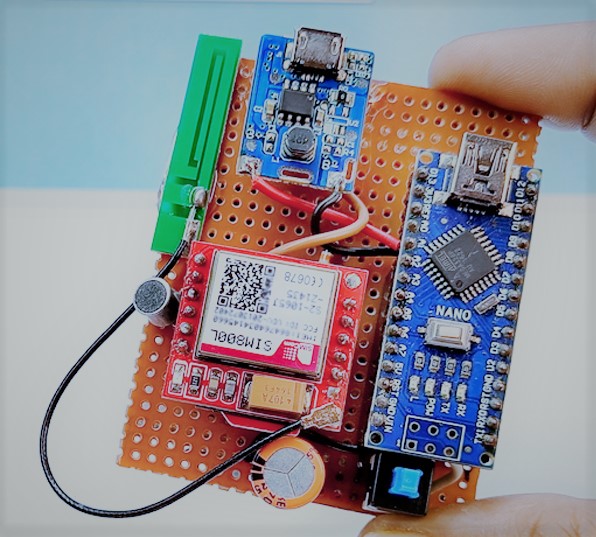
Listening Devices – aka `bugs’Technical Surveillance is the security industry term for that laypeople would normally...
The integrity of Malaysian commercial and government computer systems continues to be threatened by the increase of...
Ransomware has become a critical threat for small and medium sized businesses in Malaysia and across South East Asia...
Ever since mobile phones became an essential tool for businesspeople, their theft and resale has posed a security...
Top secret defence documents belonging to the commander of Australian operations in the Middle East stored on a USB...
The recent announcement by Google that a number of users Gmail accounts have been hacked into has ratchet up the...
Recent sales figures indicating that worldwide sales for smartphones will increase by 60% and top half a billion units...
Most people are lazy when it comes to using computers properly. People are even lazier when to comes to selecting a...
VODAFONE Australia launched an internal investigation into a security breach that has put invoicing and call records...
In late December 2010 in the US state of Michigan, a man has been charged by Police under anti-hacking laws intended...