Listening Devices – aka `bugs’Technical Surveillance is the security industry term for that laypeople would normally...
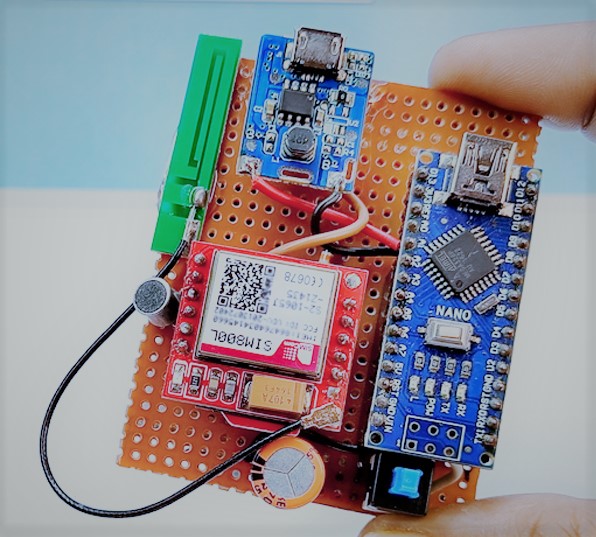

Listening Devices – aka `bugs’Technical Surveillance is the security industry term for that laypeople would normally...
Ever since mobile phones became an essential tool for businesspeople, their theft and resale has posed a security...

Mobile phone manufacturers have struggled for years to combat the problems of counterfeit batteries and phone...
We are all familiar with the news that products are counterfeited by gangs around the world; clothes, perfumes, DVDs...
McDonald’s may be the preeminent name in fast-food but that doesn’t necessarily mean that it can claim to possess the...
A number of top German companies are uniting to ban social networking sites FaceBook and Twitter from the work space....
The Malaysian consumer public has been shocked by the announcement by the Domestic Trade and Consumerism Ministry that...